Ten Critical Steps to Shielding Yourself and Your Business: A Comprehensive Guide for Enhanced Cybersecurity

In today's digital age, cybersecurity has become paramount for individuals and organizations alike. With countless threats lurking in the cyber landscape, it is imperative to take proactive measures to safeguard sensitive data and protect against malicious attacks.
This article presents a comprehensive guidebook to cybersecurity, outlining ten critical steps to effectively protect yourself and your organization. By following these strategies, you can significantly reduce the risk of cyberattacks and ensure the integrity of your digital assets.
5 out of 5
| Language | : | English |
| File size | : | 2385 KB |
| Text-to-Speech | : | Enabled |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 238 pages |
| Screen Reader | : | Supported |
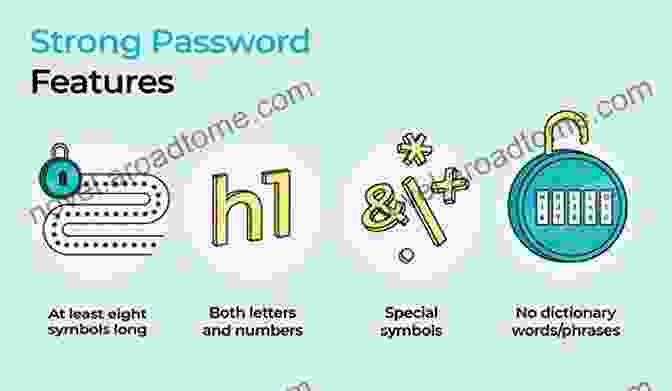
Step 1: Implement Strong Passwords
The first line of defense against unauthorized access to your accounts is creating strong passwords. Avoid using easily guessable combinations such as your name, birthdate, or common words. Instead, opt for complex passwords with a minimum of 12 characters, including a mix of uppercase and lowercase letters, numbers, and special characters.
Step 2: Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your accounts. When enabled, you will be required to provide a second form of authentication, such as a code sent to your phone, in addition to your password. This makes it significantly more difficult for attackers to gain access to your accounts, even if they have your password.
Step 3: Keep Software Updated
Software updates often include security patches that address vulnerabilities. Neglecting these updates can leave your devices and software susceptible to known exploits. Always prioritize installing the latest software updates to close any potential security loopholes.

Step 4: Use Antivirus and Anti-Malware Software
Antivirus and anti-malware software are essential tools for protecting your devices from malware and other malicious software. These programs scan your devices for threats and remove them if detected. Keep your antivirus and anti-malware software up-to-date to ensure optimal protection.
Step 5: Be Cautious of Phishing Emails
Phishing emails are designed to trick you into providing sensitive information, such as passwords or credit card numbers. These emails often appear legitimate, but they contain malicious links or attachments that can compromise your security. Always be wary of emails from unknown senders, and never click on suspicious links or open attachments.
Step 6: Backup Your Data Regularly
Backing up your data regularly is crucial in case of a cyberattack or system failure. Store your backups on multiple devices, such as external hard drives or cloud storage, to ensure that your data is safe even if one device is compromised.
Step 7: Use a Virtual Private Network (VPN)
When connecting to public Wi-Fi networks, a VPN encrypts your internet traffic, protecting your data from eavesdropping and other threats. This is especially important if you are accessing sensitive information or conducting financial transactions.
Step 8: Implement Firewall Protection
A firewall acts as a barrier between your computer and the internet, filtering out unauthorized incoming connections. Ensure that your firewall is enabled and configured correctly to prevent malicious traffic from reaching your devices.
Step 9: Educate Your Organization
Cybersecurity is a collective effort. Educate your employees about the importance of cybersecurity and train them on best practices. This includes instructing them on how to identify and avoid threats, such as phishing emails and malware.
Step 10: Protect Physical Devices
Cybersecurity measures also extend to the physical protection of your devices. Keep your laptops, smartphones, and other devices secure from theft or unauthorized access. Consider using device encryption to prevent unauthorized individuals from accessing your data if your device is lost or stolen.
By following these ten critical steps, you can significantly enhance your cybersecurity and protect yourself and your organization from a wide range of threats. Remember that cybersecurity is an ongoing process, and it requires continuous vigilance and adaptation to evolving threats. By staying informed and implementing these measures, you can create a more secure and resilient digital environment.
For a more in-depth exploration of cybersecurity best practices, consider purchasing the book "Ten Critical Steps To Protecting Yourself And Your Organization." This comprehensive guide provides detailed insights and practical guidance on how to safeguard your digital assets and minimize the risk of cyberattacks.
5 out of 5
| Language | : | English |
| File size | : | 2385 KB |
| Text-to-Speech | : | Enabled |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 238 pages |
| Screen Reader | : | Supported |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Wu Wei
Wu Wei Ryan Lindner
Ryan Lindner Rachel Deloache Williams
Rachel Deloache Williams Shazzie
Shazzie Sherry Jones Mayo
Sherry Jones Mayo Robert W Gehl
Robert W Gehl Robert W Schachner
Robert W Schachner Walter Fortner
Walter Fortner Reginald A Ray
Reginald A Ray Robert Ellis
Robert Ellis Myron Levoy
Myron Levoy Ron Jenkins
Ron Jenkins Lasa Limpin
Lasa Limpin Stuart Nicholas
Stuart Nicholas Ralph Blumenthal
Ralph Blumenthal Raffaele D Amato
Raffaele D Amato Russell Hayes
Russell Hayes Tony Medina
Tony Medina B R Burg
B R Burg Stephen Wing Kai Chiu
Stephen Wing Kai Chiu
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Lord ByronThe New Era of Healing: Revolutionary Treatment for PTSD and Traumatic Brain...
Lord ByronThe New Era of Healing: Revolutionary Treatment for PTSD and Traumatic Brain... Dylan MitchellFollow ·8.5k
Dylan MitchellFollow ·8.5k Harvey BellFollow ·10.2k
Harvey BellFollow ·10.2k Greg FosterFollow ·10.1k
Greg FosterFollow ·10.1k Johnny TurnerFollow ·11.5k
Johnny TurnerFollow ·11.5k Holden BellFollow ·19.9k
Holden BellFollow ·19.9k Connor MitchellFollow ·5.6k
Connor MitchellFollow ·5.6k Terence NelsonFollow ·11.4k
Terence NelsonFollow ·11.4k Spencer PowellFollow ·15.6k
Spencer PowellFollow ·15.6k

 Eli Brooks
Eli BrooksOver 700 Organic Remedies Shortcuts And Tips For The...
: Embracing the Power of...

 Carter Hayes
Carter HayesUnveiling the Unofficial Political Religion of India: A...
Embark on an...

 Colin Richardson
Colin RichardsonOf Colors and Critters: A Journey Through the Animal...
In the tapestry of...

 Harry Hayes
Harry HayesUnveiling the Hidden Truths: Mao, Stalin, and the Korean...
Step into the enigmatic realm of the 20th...

 George Bernard Shaw
George Bernard ShawBand 1b Pink: A Journey Through the World of Reading
Band 1b Pink is a...
5 out of 5
| Language | : | English |
| File size | : | 2385 KB |
| Text-to-Speech | : | Enabled |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 238 pages |
| Screen Reader | : | Supported |