Unlock the Secrets of Network Security Monitoring with the Ultimate Guide

The Practice of Network Security Monitoring: A Comprehensive Handbook
In today's digital landscape, protecting your network from cyber threats is paramount. Network security monitoring (NSM) plays a crucial role in safeguarding your infrastructure and ensuring the confidentiality, integrity, and availability of your data.
Introducing "The Practice of Network Security Monitoring" - the ultimate guide to mastering NSM and effectively securing your network. Written by industry experts with decades of combined experience, this comprehensive handbook provides a step-by-step approach to NSM, empowering you to detect and respond to threats with confidence.
4.6 out of 5
| Language | : | English |
| File size | : | 11452 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 376 pages |
What's Inside:
Chapter 1: Fundamentals of Network Security Monitoring
* Understanding NSM concepts and principles * Identifying key network security metrics * Establishing a baseline for network traffic analysis
Chapter 2: Network Traffic Analysis Techniques
* Packet inspection and filtering for threat detection * Intrusion detection system (IDS) and intrusion prevention system (IPS) implementation * Log analysis and security information and event management (SIEM)
Chapter 3: Threat Detection and Response
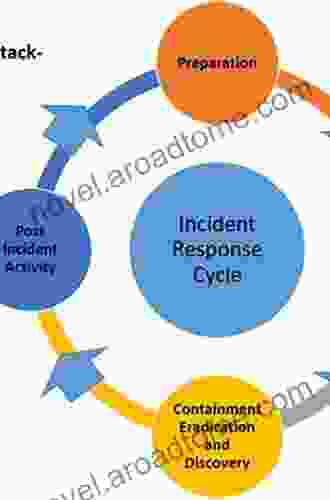
* Identifying and classifying common cyber threats * Implementing effective threat detection strategies * Establishing an incident response plan for rapid and efficient mitigation
Chapter 4: Security Monitoring Tools and Technologies
* Overview of popular NSM tools and their capabilities * Selecting and deploying the right tools for your specific needs * Integrating NSM tools into your existing security architecture
Chapter 5: Advanced NSM Concepts
* Anomaly detection and machine learning in NSM * Network visibility and network packet brokers * Cloud-based NSM and security orchestration, automation, and response (SOAR)
Chapter 6: Case Studies and Best Practices
* Real-world examples of successful NSM implementations * Proven best practices for effective network security monitoring * Tips and tricks from industry professionals
Why This Book Is Essential:
* Comprehensive Coverage: Provides a thorough understanding of all aspects of NSM, from fundamental concepts to advanced techniques. * Expert Guidance: Written by renowned security experts with extensive practical experience in network security monitoring. * Practical Implementation: Offers step-by-step instructions and real-life examples to help you implement NSM effectively. * Stay Ahead of Threats: Empowers you with the knowledge and skills to detect and respond to the latest cyber threats. * Enhanced Security Posture: Enables you to strengthen your network's security and protect your organization from data breaches and other attacks.
Who Should Read This Book:
* Network security engineers and administrators * Information security professionals * Security analysts and incident responders * Students and researchers in cybersecurity * Anyone looking to enhance their understanding of network security monitoring
Free Download Your Copy Today!
Don't wait to secure your network. Free Download your copy of "The Practice of Network Security Monitoring" now and empower yourself with the knowledge and tools to protect your valuable data and infrastructure.
Free Download Now
Image Alt Attribute
A laptop displaying a graphical representation of network security monitoring data, indicating real-time threat detection and threat mitigation.
4.6 out of 5
| Language | : | English |
| File size | : | 11452 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 376 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Richard Beach
Richard Beach Stefan Z
Stefan Z Rebecca Blanton
Rebecca Blanton Rachel Scott
Rachel Scott Steve Justa
Steve Justa Scott W Berg
Scott W Berg Ted Cascio
Ted Cascio Raffaele D Amato
Raffaele D Amato Cathy Glass
Cathy Glass Thalia Bennett
Thalia Bennett Rosie Lewis
Rosie Lewis Ralph Blumenthal
Ralph Blumenthal Wilhelm Burger
Wilhelm Burger Letizia Guglielmo
Letizia Guglielmo Roy B Blizzard
Roy B Blizzard Sarah Wilson
Sarah Wilson Warren Ellis
Warren Ellis Rodolfo Saracci
Rodolfo Saracci Robert Ellsberg
Robert Ellsberg Sandeep Balakrishna
Sandeep Balakrishna
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Deion SimmonsDelve into the Haunting World of "Her Final Breath": A Riveting Crime Novel...
Deion SimmonsDelve into the Haunting World of "Her Final Breath": A Riveting Crime Novel... Everett BellFollow ·8.2k
Everett BellFollow ·8.2k Wesley ReedFollow ·19.6k
Wesley ReedFollow ·19.6k Thomas PynchonFollow ·4.2k
Thomas PynchonFollow ·4.2k Henry GreenFollow ·14.4k
Henry GreenFollow ·14.4k Darnell MitchellFollow ·19.8k
Darnell MitchellFollow ·19.8k Ron BlairFollow ·14.4k
Ron BlairFollow ·14.4k Colt SimmonsFollow ·19.2k
Colt SimmonsFollow ·19.2k Ben HayesFollow ·15.6k
Ben HayesFollow ·15.6k

 Eli Brooks
Eli BrooksOver 700 Organic Remedies Shortcuts And Tips For The...
: Embracing the Power of...

 Carter Hayes
Carter HayesUnveiling the Unofficial Political Religion of India: A...
Embark on an...

 Colin Richardson
Colin RichardsonOf Colors and Critters: A Journey Through the Animal...
In the tapestry of...

 Harry Hayes
Harry HayesUnveiling the Hidden Truths: Mao, Stalin, and the Korean...
Step into the enigmatic realm of the 20th...

 George Bernard Shaw
George Bernard ShawBand 1b Pink: A Journey Through the World of Reading
Band 1b Pink is a...
4.6 out of 5
| Language | : | English |
| File size | : | 11452 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 376 pages |